Appguard Management Service¶
1. Introduction¶
Authentication and authorization are the quite essential features for any application. On boarding new user, login/logout of user, assigning role, creating role-based access control of application resources are the standard requirements for any application. Also, there are many authentication mechanisms such as username/password-based authentication or password less OpenID.
An application must implement various ways for user authentication. This requires the application developers to strategize and develop flawless user authentication mechanism. Even after secure login, there is further needed to protect some application resources based on user role or to implement unauthorized access of some resources. This requires a policy driven access control system that can act once user is authenticated. Developing and maintaining these essential features require tremendous amount of effort, skill, and time. Major effort comes with database design, software design, interface with third-party provider, quality secure code development, testing etc.
TCUP App Guard Management is an authentication and authorization service which helps to add authentication and authorization in applications without much effort. It reduces development time from month to days and delivers quality secure code which is tested and developed by experts. App Guard provides user federation, strong authentication, user management, fine-grained authorization etc. with a pragmatic set of APIs which can be used in application.
The following is a detailed diagram for Appguard Management service:
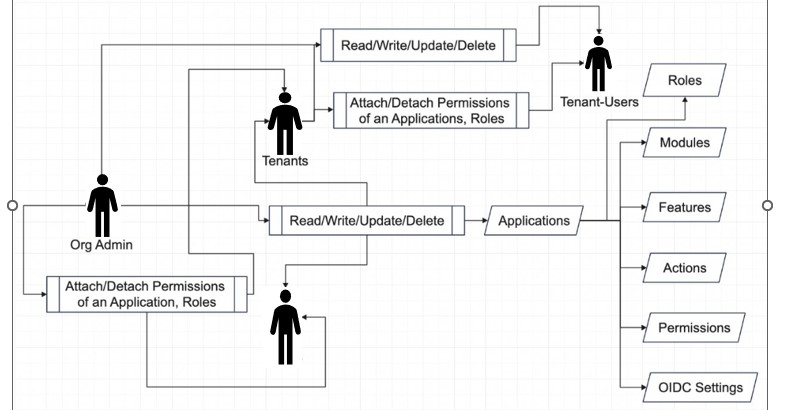
1.1 Intended Audience¶
The intended audience of this document are developers who wants to have an overview of TCUP App Guard Service. After reading this document, the user will understand the capability of TCUP App guard Service.
2. Key Concepts¶
In order to use Certificate Management Service, a user needs to understand some of the basic concepts of the service. Please refer to the following section:
Every App Guard installation has at least one user defined once the installation is complete. This user is called “Org Admin”. The “Org Admin” user can only be created by host operating system administrators having special privileges. The “Org Admin” user is a super user, and it is used for creating application, creating user, creating tenant and other platform related administration work.
2.2 Tenant Admin (hereby referred simply as “Tenant”)¶
Application can create as many tenants aka customers per application. Each tenant is administered by a tenant specific administrator called “Tenant”. The “Tenant” user is created by the “Org Admin” through the App Guard administration portal or API.
2.3 Tenant sub-user¶
Under each application, tenant sub-user can be created. This is done by the tenant admin. For each created user, fine grained access control policies can be defined within the App Guard service. All users have their own credentials (username and password) and JWT keys to access authorized services.
2.4 User¶
Under each application, users can be created. This is done by the org admin. For each created user, fine grained access control policies can be defined within the App Guard service. All users have their own credentials (username and password) and JWT keys to access authorized services.
2.5 Role¶
App guard application role is collections of similar policies (set of permissions). “Tenant” can create a role definition per application and the role can be attached to any user. For example, an administrator role can have all the access privileges whereas a developer role might not have access to certain services.
2.6 Modules¶
Module can be defined as an individual resource inside any application or can also be considered a single component. For example, Billing, Shipping, purchase can be considered as a module. These module details need to be registered with App Guard and each module consists of multiple features. A module can have specific action like (allow, deny, read, write) permissions to access particular resources.
2.7 Features¶
Features can be defined as a subcomponent of an application under a module. Each module can have multiple features. For example – invoice, tax etc. can be a feature of a billing module. Each feature can have specific action like (allow, deny, read, write) permissions to access particular features.
2.8 Action¶
Action defines a set of activity name which can be applied to specific features or modules. For example, allow, deny, read, write is an example of action.
2.9 Permission¶
Permission is an access control for a particular application. In App Guard, a permission consists of three components like object, action, and resource. Here Object is real world entity like module or features on which some action like allow or deny is given to a particular user. Tuple based permission is supported. Permission must belong to any of the modules or features, action and user created in App Guard.
3. Functional Capabilities¶
AppGuard Management Service have the following functional capabilities:
Org Admin - Create and delete user, tenants, role, permission - Complete access to the portal - Assign/detach role to tenant - Create/delete permission
Tenant - Create/delete users/role - Assign/detach role to tenant users - Create permission for tenant users
Tenant sub-user (tenant_user) - Users cannot create/delete any elements in App Guard under a tenant. They can get a view of the roles, and permission assigned to it, if any.
User - Users cannot create/delete any elements in App Guard. They can get a view of the roles, and permission assigned to it, if any.
4. Purpose/Usage¶
App Guard provides user federation, strong authentication, user management, fine-grained authorization etc. App Guard provides a beautiful set of APIS which can be used in application
5. Examples¶
Consider an example of creating an application and create user and permission for user to login to get an access key to access application’s resources like API. The steps required to create a register application and create a tenant is as follows:
The Organization admin needs to register an application through App Guard portal or through API providing application name and callbackURL.
A unique app ID will be created. Developers need to make a note of that key as it is required later.
Organization admin then needs to create a new tenant by providing a username and password. Tenant needs to verify the email address and admin needs to activate the account before login.
Tenant can then create sub-tenant as required with previous steps.
A module and sub subsequent features and actions should be defined under application.
The tenant creates a new permission by add module/features with actions to users
Once, tenant or sub-tenant is logged in, they will receive three keys, ID Token, Access Token and Refresh Token. Access Token will be in JWT format, and it will contain all necessary permission set by admin for this user. Application can then restrict or allow resources based on permission received in JWT
6. Reference Document¶
For more details about this service please refer the following documents
User guide
API Guide